Below are current information security advisories. If you have any questions, please email infosec@nova.edu.
July 2024 – AT&T Security Breach
On Friday, 7/12/24, AT&T published a notification about a recent data security breach that has affected AT&T wireless customers.
Per their disclosure, in April 2024, AT&T discovered that hackers had accessed call logs and SMS text message records for nearly all of its cellular customers between May and October 2022, as well as for January 2nd, 2023. While the content of calls and texts was not compromised, the data does reveal phone numbers that AT&T customers interacted with during that period.
While AT&T has stated that they believe the data is not publicly available, it is essential to remain vigilant and take steps to protect yourself.
Recommendations:- Be Wary of Suspicious Activity: Be cautious of unsolicited calls, texts, or emails, especially those requesting personal information or urging immediate action.
- Monitor Your Accounts: Regularly review your financial and other online accounts for any unauthorized activity.
- Enable Strong Security Measures: Ensure your phone and computer have the latest software updates and strong, unique passwords.
- Consider a Credit Freeze or Fraud Alert: You may want to consider placing a credit freeze on your credit report or setting up a fraud alert with the major credit bureaus.
We understand that this news may be concerning. Please know that we are committed to your security and well-being. If you have any questions or concerns, please do not hesitate to contact our Information Security team (infosec@nova.edu; 2-0732).
For more information about the breach and steps you can take, please visit the AT&T website at about.att.com/pages/data-incident.html.
Keeping Zoom Secure
You may have heard the phrase “Zoombombing” recently talked about in the media. It is a disruptive practice of that seeks to disturb online meeting sessions by displaying offensive graphics, messages or broadcasting disruptive audio. You can think of this like a prank telephone call, but the results could be disastrous since you can’t erase or undo what happens, and all attendees will be part of it.
To protect your online classroom environment, please be sure to update your Zoom software and implement the following suggestions when scheduling and hosting Zoom sessions.
Update your Zoom software
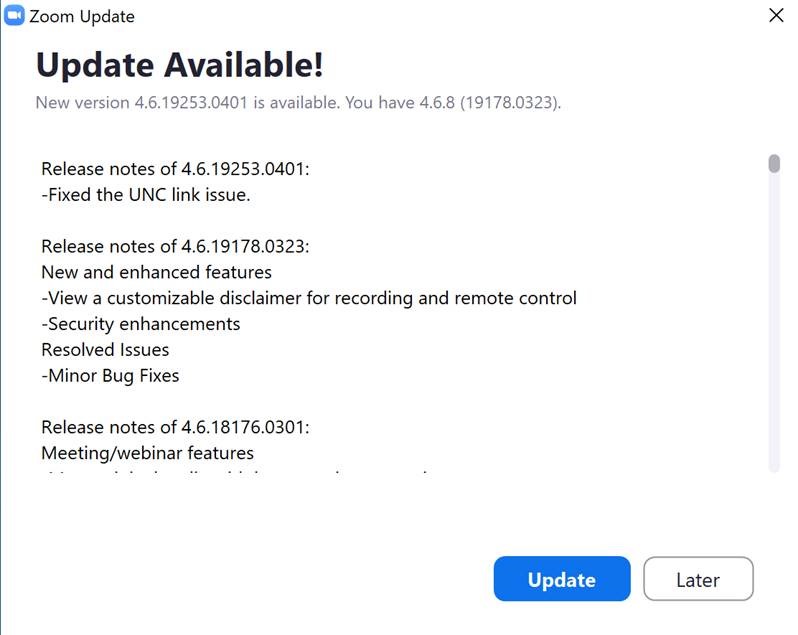
An important update for the Zoom application was released April 2nd, 2020 that fixes a recently identified security vulnerability. As a result, OIIT urges you to update your application in order to ensure platform safety, privacy, and security.
To update Zoom, open the Zoom application on your Windows or Mac personal computer. You will see up to two different notifications alerting you of an application update.
The first notification is a pop-up window that will appear with the "Zoom Update" (pictured below).
The second notification will appear on your Zoom application home screen. A light blue stripe is visible with verbiage that reads, "A new version is available! Update."
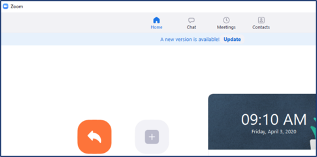
Click the "Update" button in either area and follow the onscreen prompts to complete the process.
Additional Security for Zoom Hosts
Your primary methods to ensure safety with Zoom meetings should be:
- Only allowing attendees you expect in your session
- Not allowing unintended video, audio or screen sharing
- Moderating or removing disruptive attendees
To accomplish these goals, we have the following recommendations on Zoom meetings:
Never share meeting URLs on public-facing sites or services
Do not share your meeting URL on public-facing sites like social media or forums. Students can access Zoom meetings in Canvas from the Course Menu; if necessary, you can provide the meeting details by emailing or messaging participants directly.
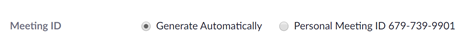
Don’t use a Personal Meeting ID
The Meeting ID is the ID used in a Zoom meeting URL. It is best practice to allow Zoom to generate this automatically, and do not use the same ID each time.
Turn off participant video and audio by default, and mute users on entry
To avoid attendees (including yourself) from being seen or heard before you are ready, we recommend not enabling video or audio by default. Additionally, you should mute all participants on entry.

![]()
Use Waiting Rooms when you feel additional security may be warranted
You can enable a waiting room for your meeting, which allows you to decide who will enter the session.
Co-host permissions
Due to a change for education customers, screen sharing is not enabled by default for every participant in a session. The host can determine who can share their screen by making those who wish to share a co-host. Always be cautious about who you give co-host permissions, as they have the ability to moderate participants and share whatever they like on screen.
Moderate your participants
When hosting a Zoom session, it is important to understand the controls provided by Zoom to moderate participants, such as muting, stopping video, putting participants on hold/in waiting room or removing them. You might consider adding another trusted user as a co-host to help you moderate, especially in larger meetings.
Click the Manage Participants button to see the Participants pane:
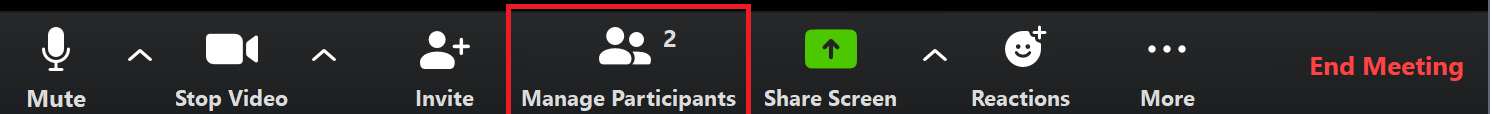
At the bottom of the Participants pane, you have options to mute all, unmute all along with some additional participant options, such as locking the meeting so that no one else can join:
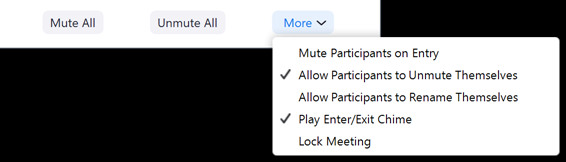
For each individual participant, you can mouse over their name, and use the Mute button or the More button for asking to start video or stop video (if video is enabled), put a participant on hold, or remove them from the session:
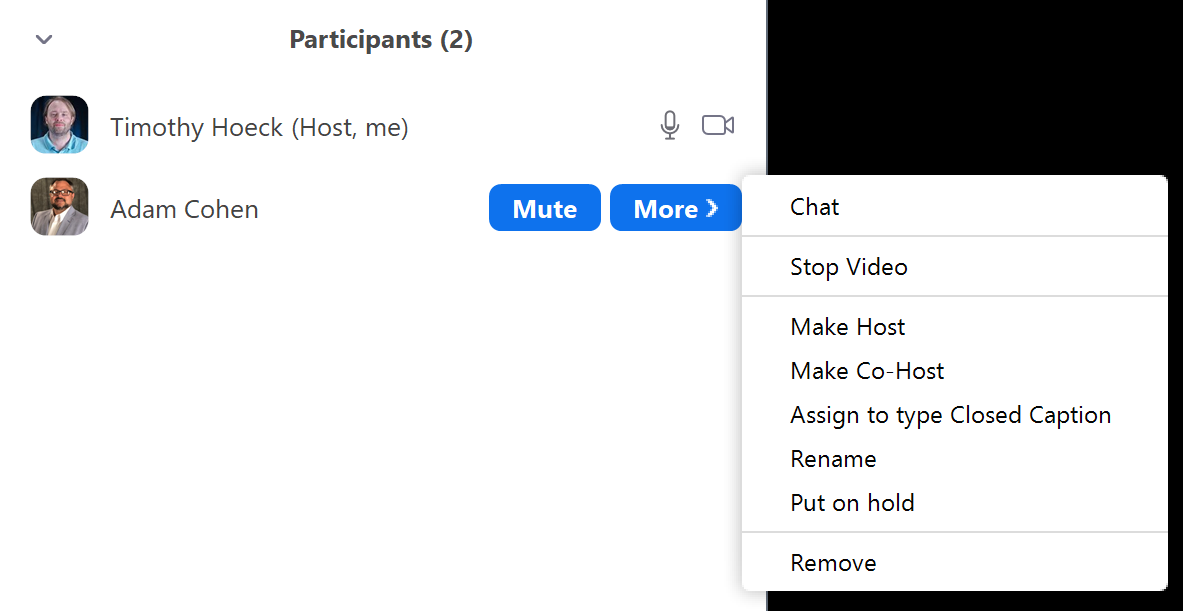
For more information on managing participants and breakout rooms, see the following Zoom articles:
Managing Participants in Meeting
Further Zoom Resources
Zoom Tips Shared in a Previous LEC Article
Scammers Replicate Third Party Payment Website
Many online shops give the option to complete your transaction through third-party payment sites (e.g., PayPal, Visa Checkout, Google Pay, Apple Pay, etc.). If you shop online at a website that redirects you or has a pop-up window appear, be sure to take a close look at the domain to ensure that you're not being conned.
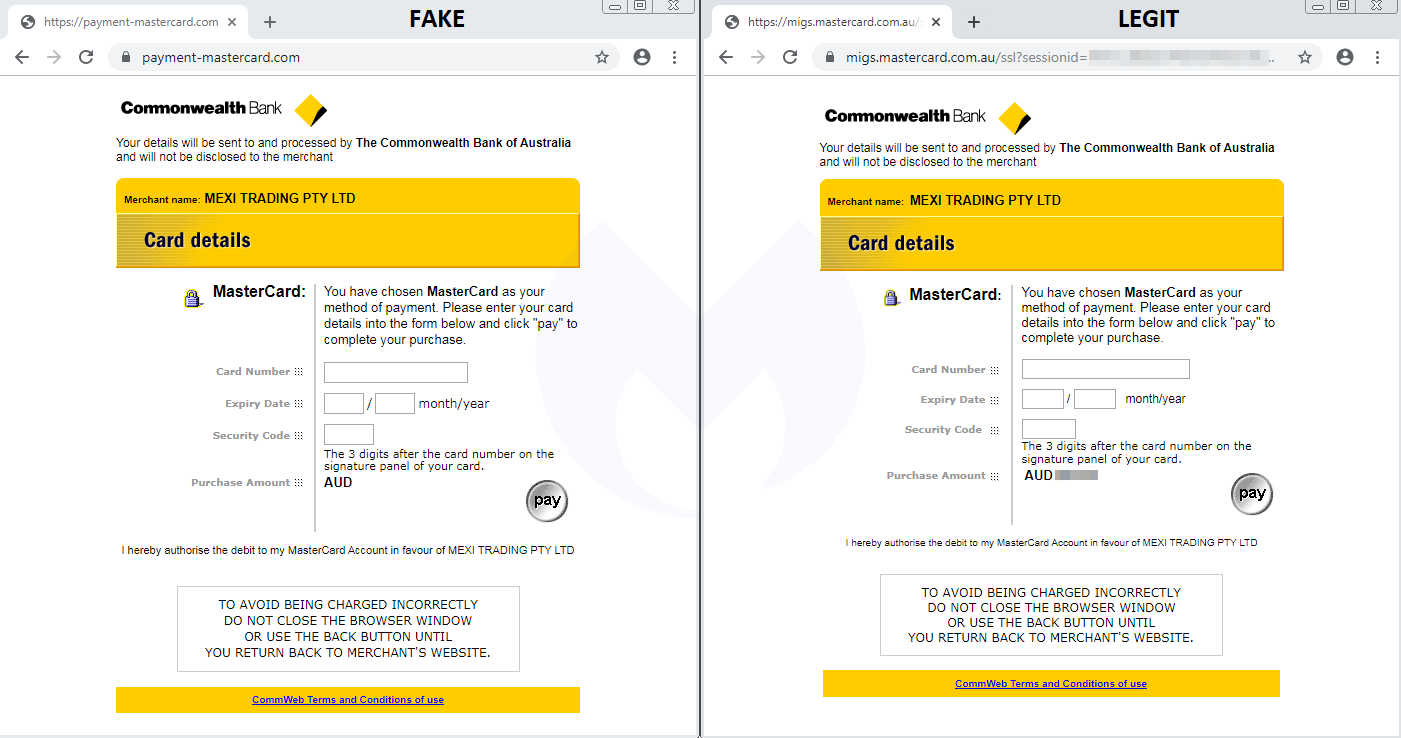
In this image: A side-by-side comparison shows how the fake processor looks versus the real one. There is virtually no difference in appearance save for the domain, which is "payment-mastercard.com" on the fake one and "migs.mastercard.com.au" on the real one. Image courtesy of Malwarebytes.
One of the most common methods hackers use to steal information is infecting a merchant's checkout page with malware that "skims" or gathers personal data. This new method is similar in that the hacker adds bad code to a shop's site, but instead of skimming information, it redirects you to a fake site to pay the hacker directly.
While there is only one known instance of this happening (to a shop in Australia), this could be a trial run for a much larger operation.
Source: Ars Technica